Understanding the Basics of the JWT Tokens
Sending your payload using JWT Token is like sending your object in a transparent box locked with a highly secure shared key.
If someone changes your box, you wont be able to open it.
If you are able to open it, you can safely say that the object is genuine- no one has changed it on the way.
JSON Web Token (JWT) is an open standard where two parties can exchange JSON payloads in a trusted way. Both parties can trust each other on the exchanged payload because it is digitally signed using a shared secret key or a public\private key.
The key thing to remember is that the JWT token do not protect your data, but only ensures it’s integrity. Hence, if we are able to verify a token, it means no one has tampered the payload in it. We would require additional encryption for protecting the payload data.
We have a separate article on its usage in authorization process. But, in this article, we will keep our focus only understanding the data in the token and exploring why should we trust it ?
Decoding the Token
Below is an example of JWT Access Token, containing an authorized user detail.
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6InRlc3RBZG1pbiIsInJvbGUiOiJhZG1pbiIsImlhdCI6MTYwNjk1MDQ5MywiZXhwIjoxNjA2OTUwNDk4fQ.Vfr4M31jkqT5u4BqbDqNQaEtZ1Sqbwwy7zS7jw94CC0
If we look at the token above, it has 3 sections. The last part is the signature whereas the first two parts are the base64 encoded Header and the PayLoad.
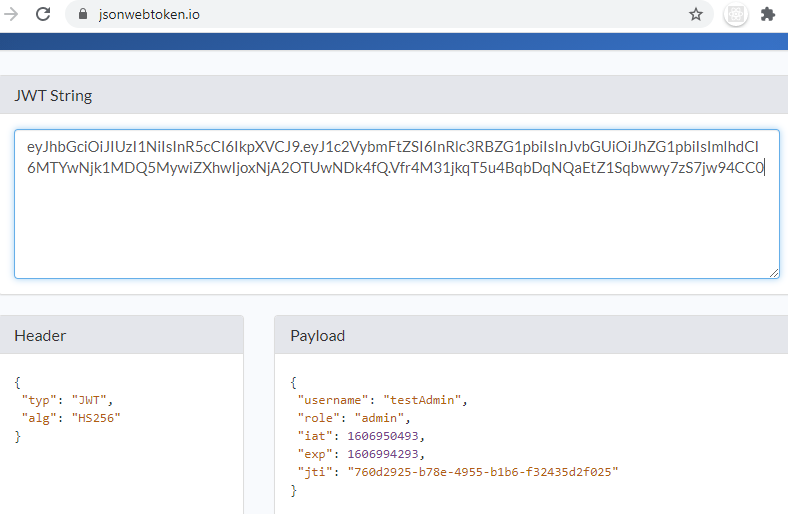
Hence, clearly the header and payload are not protected and the above figure shows their actual content.
- The header contains the encryption algorithm used in the signing process.
- The payload, here, includes the user detail, his role and an expiry time for the token.
Why should we trust these tokens ?
Of course, these tokens do not protect the content but definitely ensures it’s integrity. The below diagram shows how ?
As we can see, both the signing authority and verifying client, try to re-create the signature on the message. They use the same encryption algorithm as it is shared inside the token header.
- Only if both have the shared secret key or a matching public\private certificates, the generated signatures will match.
- First, this ensures no other than the targeted client is able to verify and, hence, use it as a valid data.
- Second, a verified token also confirms that it has come from the signing authority holding a matching secret.
- Finally, if any one tampers the message or the signature, the signatures won’t match and the verification will fail.
Summary
In short, a successfully verified JWT token ensures that -1. No one has tampered the payload and 2. It has come from the right authority.
As regards the protection of the payload data, we can use another layer of encryption over the token.
The article on using JWT Access Token for Authorization shows a practical usage along with a simple POC on this signing and verification process.